SIEM correlations produce alerts that you have to respond to. Over time you start seeing trends of the things that happen most frequently. Those become then the opportunities for orchestration.
Security Orchestration is a coordination of actions across disparate security tools, many of them from different vendors. When you analyze an incident, there’s a sequence of actions that each tool performs.
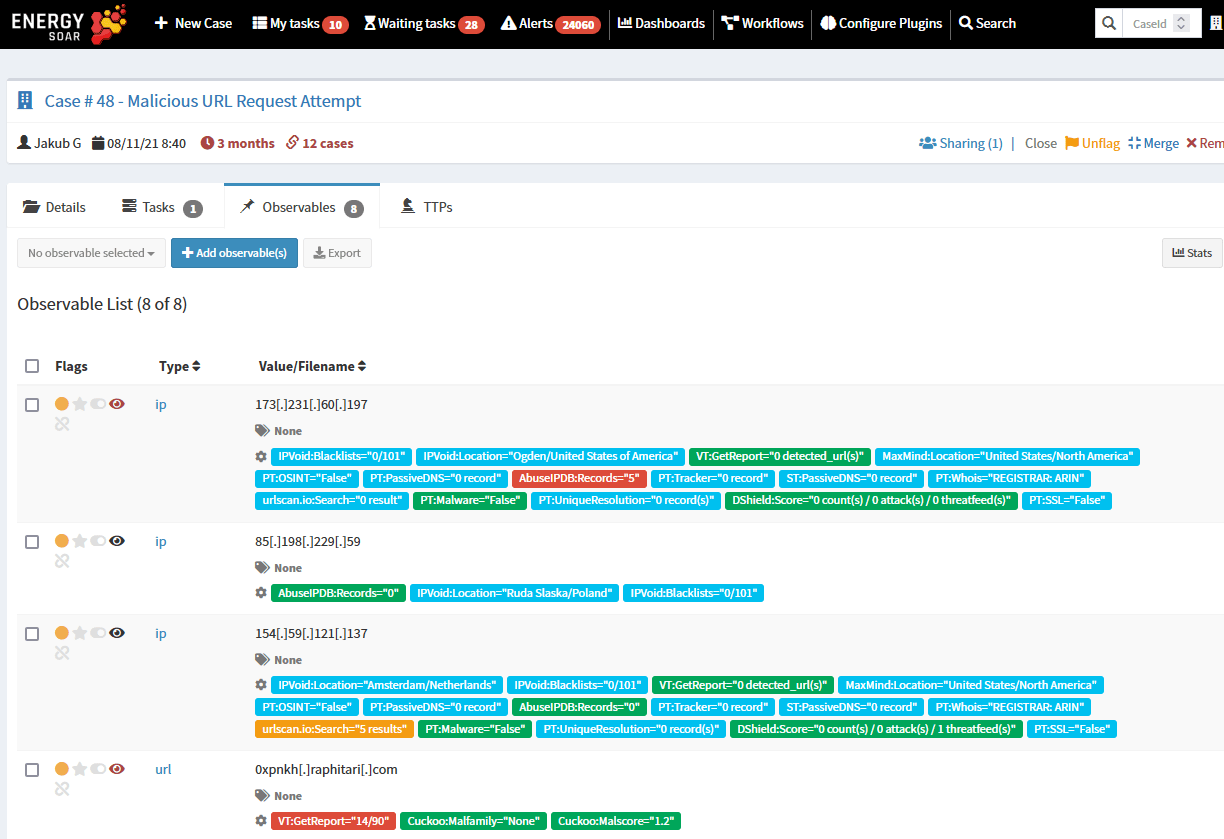
Energy SOAR integrates with tools through plugins. There are two types of integrations.
1. Analyzers – for instance:
- Check file or url in a sandbox,
- Check file reputation in Virus Total,
- Geolocate an IP,
- Check file against YARA rules.
2. Responders – for instance:
- Disable a user in identity and access management platform,
- Tell Symantec Endpoint Protection to quarantine an endpoint,
- Tell a Check Point firewall to block an IP,
- Block an IP on a host via Energy Logserver SIEM agent.
So Energy SOAR is allowing the security analysts to coordinate all of those actions across your tools.
It’s like a symphony orchestra. The tools are different instruments, each has a disparate role to make music, and Energy SOAR is a conductor, making sure that everything is playing right way and on time.
What orchestration actions should we look at first?
Look for those events that are happening frequently, the ones that require many actions using different tools. The orchestration that you run around these is going to save your time.
You’ve made the investment in other technologies so you can tie them together and integrate.
Start with contextualization, those actions that just do information gathering. Then deeper dive into responses. Finally orchestration leads to more mature security automation strategy in your organisation.