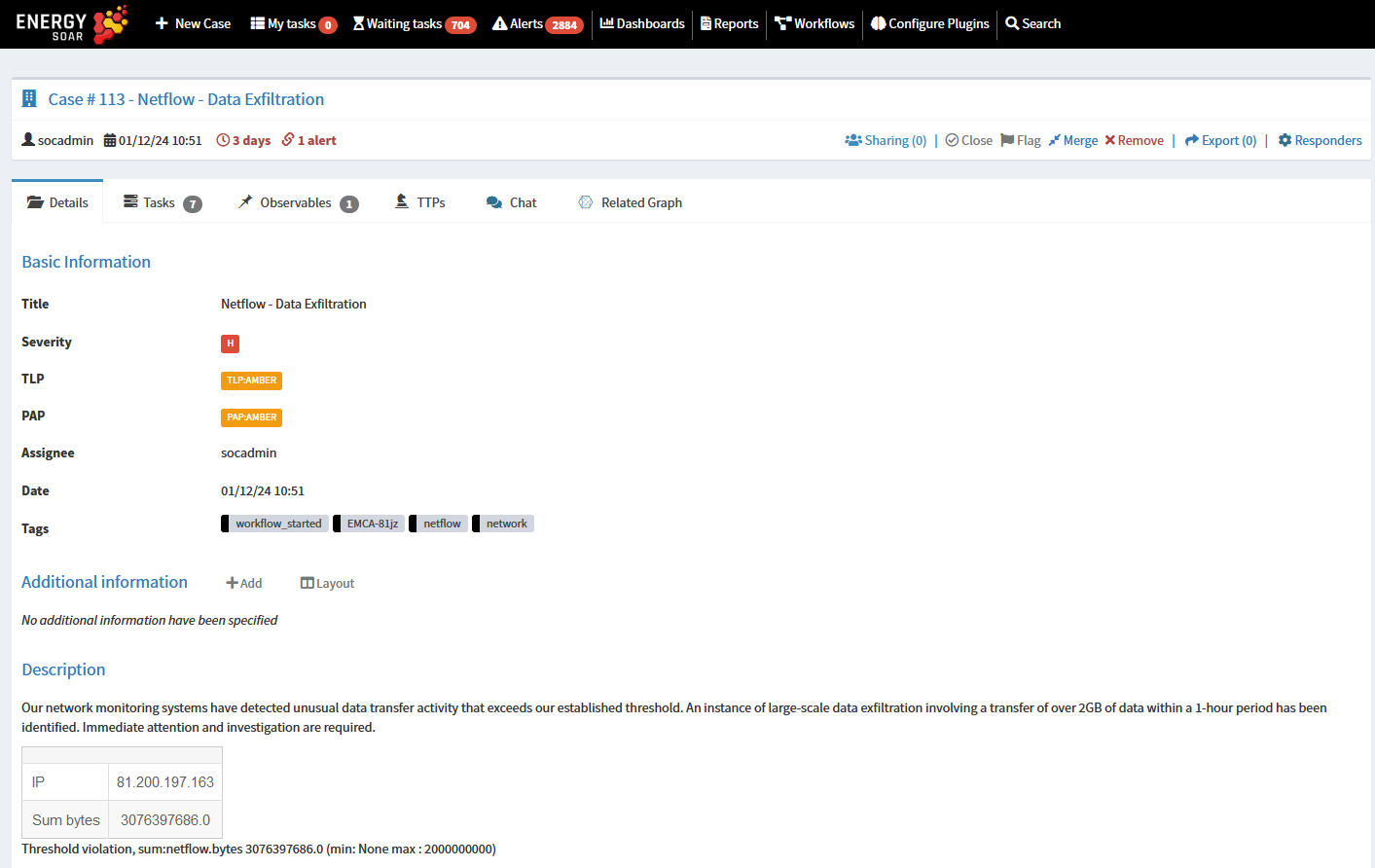
You can use network monitoring system or SIEM to detect unusual data transfers that exceeds established thresholds. It could indicate a potential data exfiltration attempt. Immediate attention and investigation are essential.
Once a new alert is generated, a Security Orchestration, Automation, and Response (SOAR) system can be used to automate and streamline the investigation process, helping security teams respond promptly and effectively to the incident.
This approach aims to enhance the organization’s ability to detect and respond to security threats in a timely and efficient manner.
Let’s discuss how does it work in Energy SOAR.
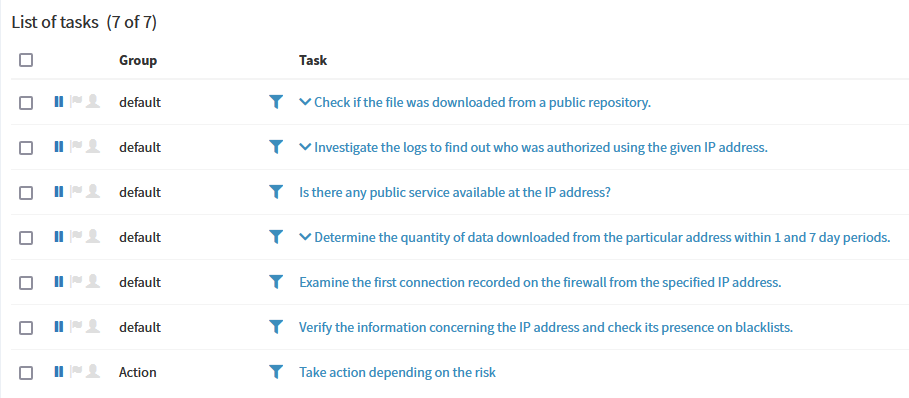
Energy SOAR provides appropriate case template, which includes set of tasks to analyse the event step by step:
Check if the file was downloaded from a public repository
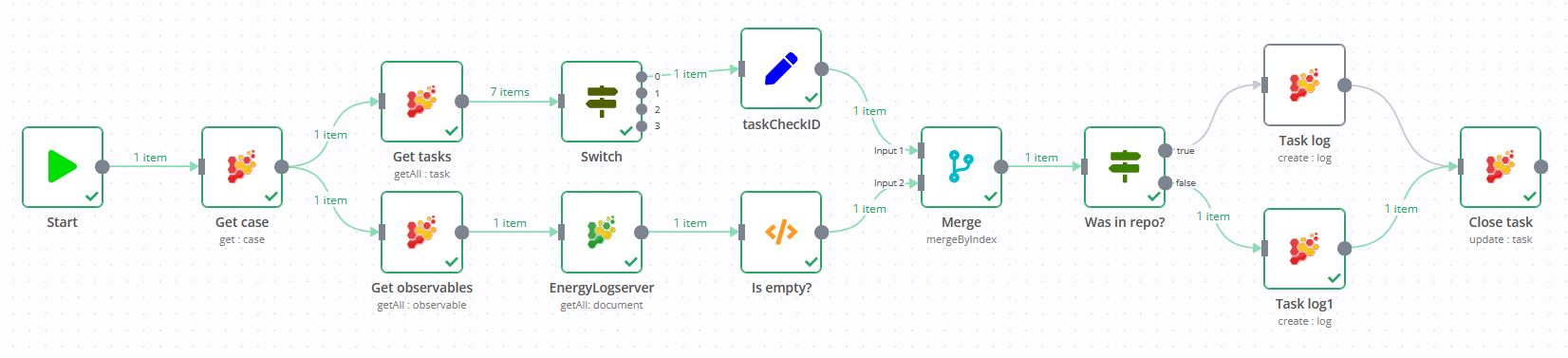
Upon receiving an alert based on flow data indicating an unusual data transfer, the initial step is to investigate the origin of the traffic. This involves checking the web server logs to see if the file was downloaded from a public repository, which is often a legitimate source for big files. To streamline and automate this investigative process you can run responder, equipped with a predefined workflow.
As you can see there is an Energy Logserver node which allows querying web server logs gathered in the SIEM. Results are added to the case as task log, so an analyst can view the details immediately.
Determine the quantity of data downloaded by the particular address within 1 and 7 day periods
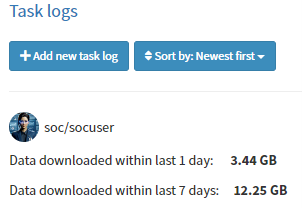
Next we want to verify, how much data was downloaded by the particular host. An assigned workflow is used to perform the verification. This workflow includes querying the SIEM for aggregated metrics and recording the results. The output of this verification process is then displayed in a task log, providing a clear and organized view of the data download activities by the specified host within the defined time windows.
This is the way how analyst can complete the tasks one by one. We can go even further and enable automatic workflow execution just after creating new Netflow-Data Exfiltration case, so an analyst can review results and take relevant actions to respond the event.
Finally Energy SOAR lets you assign automated response to block network traffic.
This integration of automated workflows and responses enhances the efficiency and effectiveness of incident response, allowing for faster detection and mitigation of security threats.