MISP is an open-source threat intelligence platform designed to improve sharing of structured threat information. MISP is particularly focused on sharing information about malware and other cyber threats among computer security professionals and organizations. This collaborative approach helps the community stay informed about emerging threats. MISP uses a standardized data model to represent threat information in a structured and consistent manner. This allows for better interoperability and integration with other security tools. MISP supports automated information sharing, allowing organizations to exchange threat data in real-time. This helps in creating a more dynamic and responsive defense against cyber threats.
MISP supports automated information sharing, allowing organizations to exchange threat data in real-time. MISP can be integrated with other security tools, such as IDS, SIEM and SOAR solutions to enhance overall cybersecurity capabilities. In this article we will dive into integration with Energy SOAR.
You can integrate Energy SOAR and MISP in multiple ways.
Query MISP and bring events to Energy SOAR
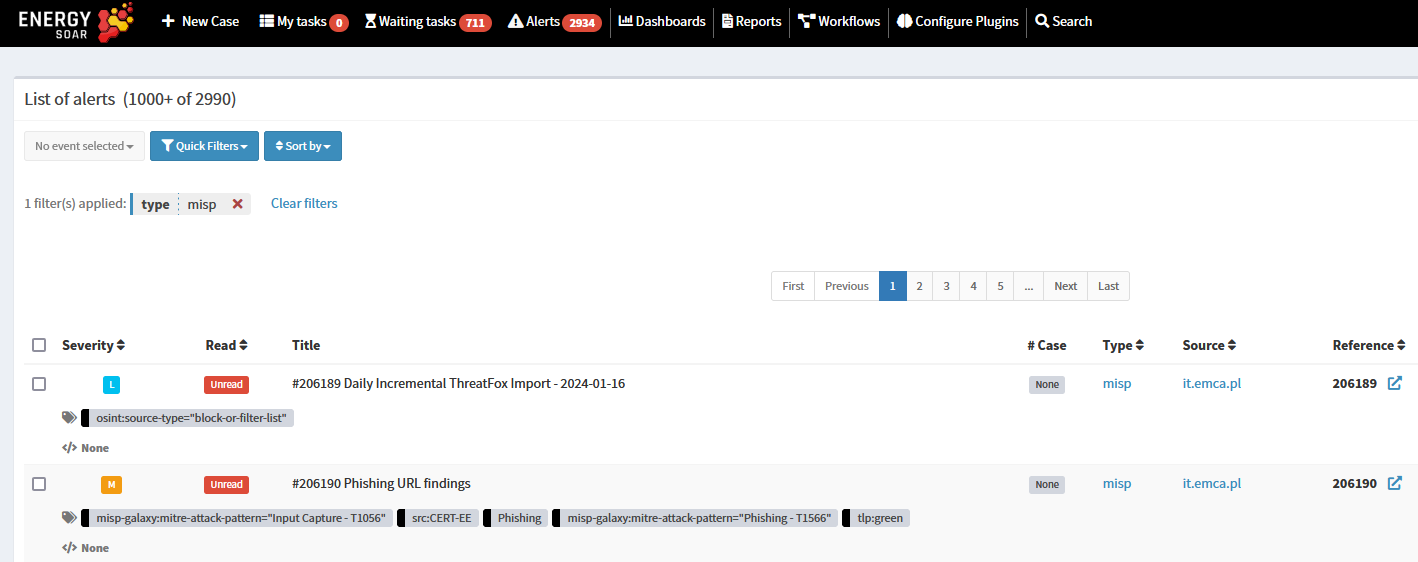
Energy SOAR is querying MISP in selected interval e.g. 1 hour for new events that have been published. Events are stored as alerts and contain all relevant information. You also get a link in reference section to open the event in MISP instance directly. So we only need to keep eyes on Energy SOAR and when a new event is published to MISP it is automatically brought in.
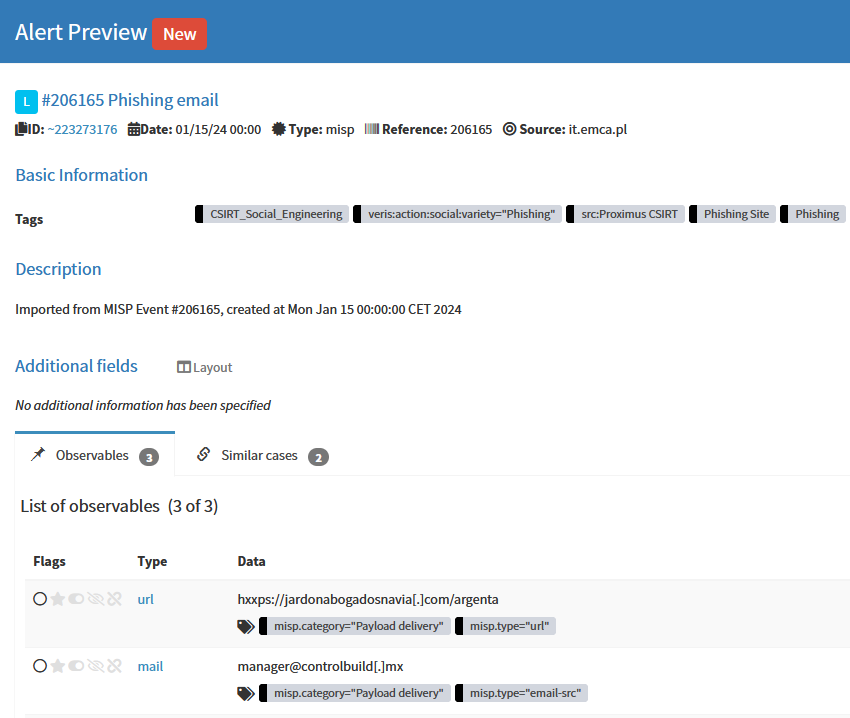
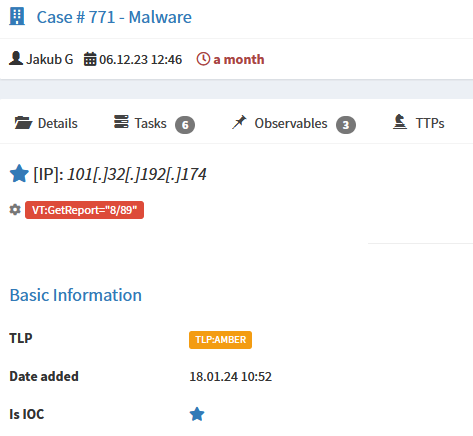
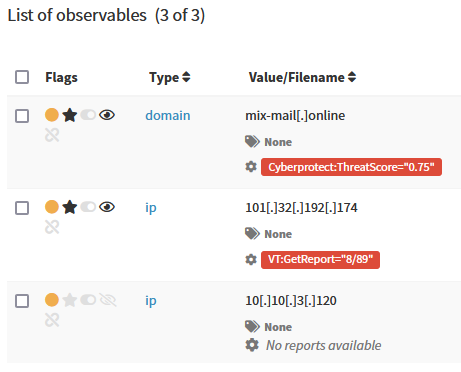
Once a new alert is created Energy SOAR is parsing out all of the observables and metadata.
Using Similar cases module we can quickly correlate events from other sources with MISP events where we observe the same objects such as IP addresses. For example when you investigate SSH brute force attempt you can see if origin IP is associated with MISP events.
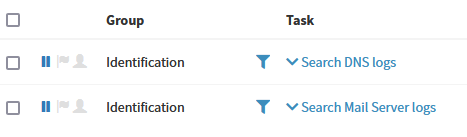
Let’s import the alert as a new case and use Phishing MISP findings playbook. The playbook provides tasks such as Search DNS logs and Search Mail Server logs which have workflows assigned beneath:
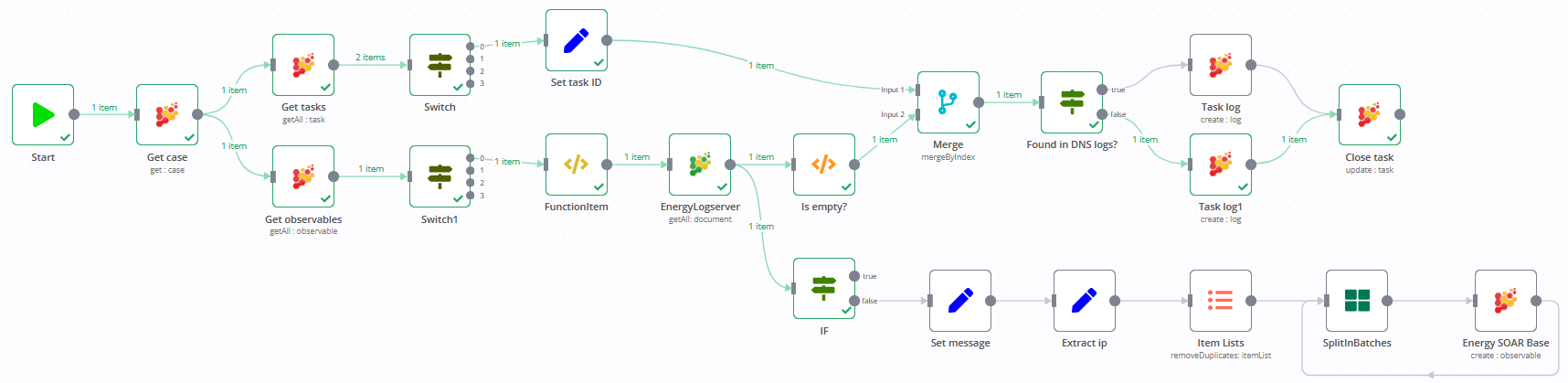
Workflow EnergyLogserver – Search DNS logs will query Energy Logserver index to verify if DNS clients send requests for domains included in the case. Workflow will also extract domains from URLs if needed.
When there is a match in DNS logs, then client IPs are added to observables.
The same way we use workflow EnergyLogserver – Search Mail Server logs to search logs for e-mail addresses from the case. When there is a match, then e-mail receiver is added to observables.
Export cases from Energy SOAR to MISP
Because we have two-way trust, we can also push cases originated within Energy SOAR to MISP. For example if we have an Energy Logserver alert brought into Energy SOAR and it came with a bunch of observables we deemed to be malicious, then we can push the case to MISP form Energy SOAR console smoothly. During that we will also bring in observables.
To strip personal information such as hostnames or internal addresses you can use IOC flag to mark observables you want to publish.
IOC flag (black star) indicates observables classified as True Positive. Only IOC-flagged observables are exported to MISP instance.
MISP analyzer
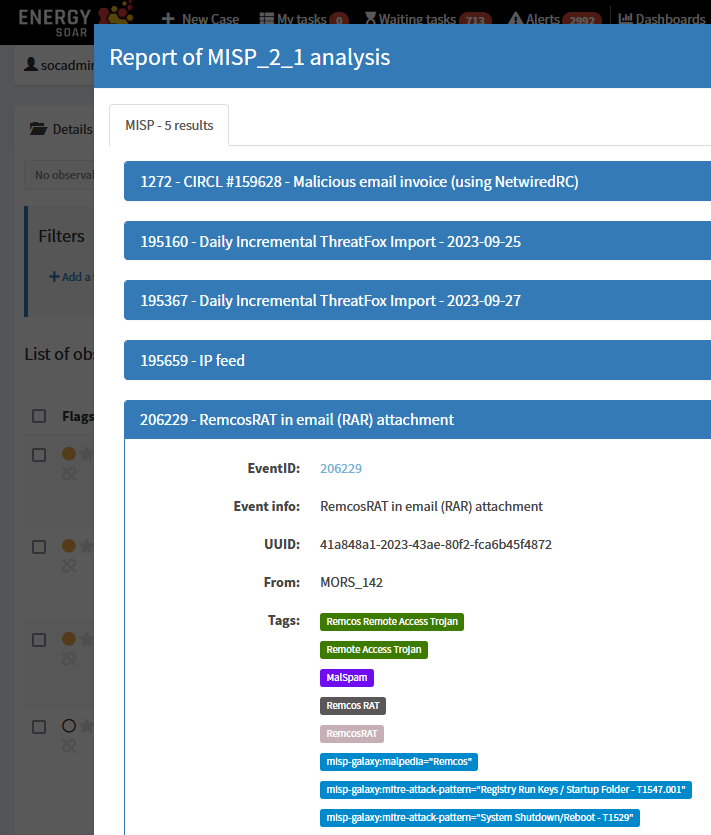
MISP analyzer lets you to query MISP instance from Energy SOAR console for events containing selected observables such as: domain, IP, hash, etc. So analysts don’t waste their time on manual searching.
If we run the analyzer we will immediately see all events related to the observable. EventID link points directly to MISP instance to see additional details e.g. APT group, malware family and other associated IOCs.
Use MISP Warning Lists
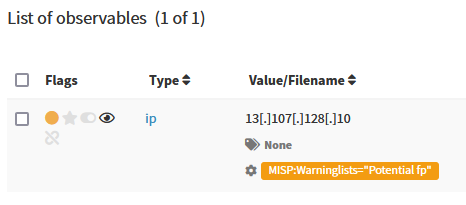
MISP Warning Lists are lists of well-known indicators that can be associated to potential false positives, errors or mistakes.
For example you can find there:
- List of known Office 365 IP address ranges,
- List of known Amazon AWS IP address ranges,
- List of known Windows 10 connection endpoints,
- List of known Microsoft domains,
- List of known Tenable Cloud Sensors,
- Specialized list of vpn-ipv4 addresses belonging to common VPN providers and datacenters,
- and many more.
You can insert warning lists entries into database for higher performance and schedule updates to get current content.
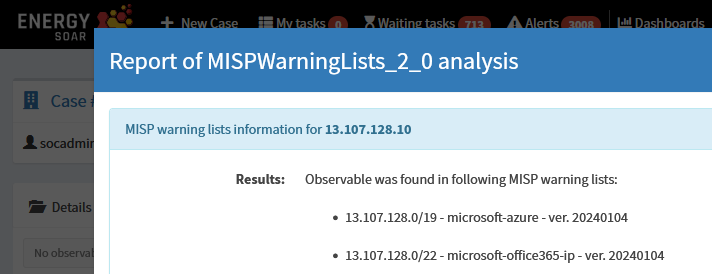
Energy SOAR analyzer lets you check observables against MISP Warning Lists to identify false
positives very quickly:
Full report points to specific list details:
Each way of Energy SOAR integration offers different capabilities and the way you choose depends on the specific use case. You can also execute MISP and MISP Warning List analyzers automatically using workflows just after a new alert is created to speed up handling events even further.