Splunk App allows to take many different actions:
- You can retrieve information from Energy SOAR about alerts and cases that were created.
- You can retrieve information from Energy SOAR about jobs that are being performed by analyzers.
- You can create a new alert or a case from Splunk in Energy SOAR.
- You can run analyzers from Splunk in Energy SOAR.
Configuration
An account is used to authenticate to Energy SOAR instance. You need to provide username and a valid API key. Then add Energy SOAR instance: host, port, URI.
Cases dashboard
The application integrates a preconfigured dashboard with searches allowing you to easily interface with Energy SOAR.
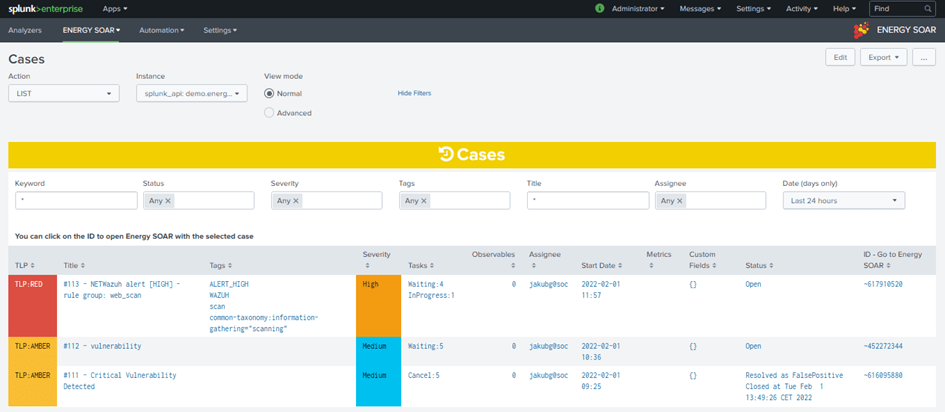
You can retrieve the history of cases in Energy SOAR using the action “LIST”. For each job, you can see :
- TLP: TLP of the case
- Title: Title of the case
- Tags: Tags of the case
- Severity: Severity of the case
- Tasks: Tasks of the case by status
- Observables: Number of observables for the case
- Assignee: Current assignee for the case
- Start Date: Date and time for the start of the case
- Metrics: Current metrics for the case
- Custom Fields: Current custom fields for the case
- Status: Current status for the case with detailed resolution
- ID: ID of the case
You can click on the ID to view case details directly on Energy SOAR.
You can set filters:
- Keyword: A keyword to search on
- Status: Status of the case
- Severity: Severity of the case
- Tags: Tags of the case
- Title: Title of the case
- Assignee: Assignee of the case
- Date: Creation date of the case
Create a new case
You can create a new case from Splunk using the “CREATE” action.
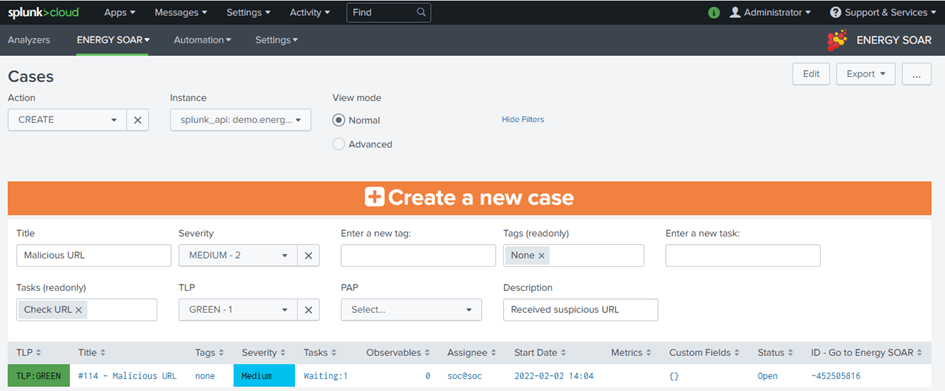
Title: Title for this new case
Severity: Severity for this new case
Tags: Tags for this new case (they are added by specifying values in the “Enter a new tag” input)
Tasks Tasks for this new case (they are added by specifying values in the “Enter a new task” input)
TLP: TLP for this new case
PAP: PAP for this new case
Description: Description for this new case
The search will create the new case and return information such as the case ID.
Alerts dashboard
The application integrates a preconfigured dashboard with searches allowing you to easily interface with Energy SOAR and alerts.
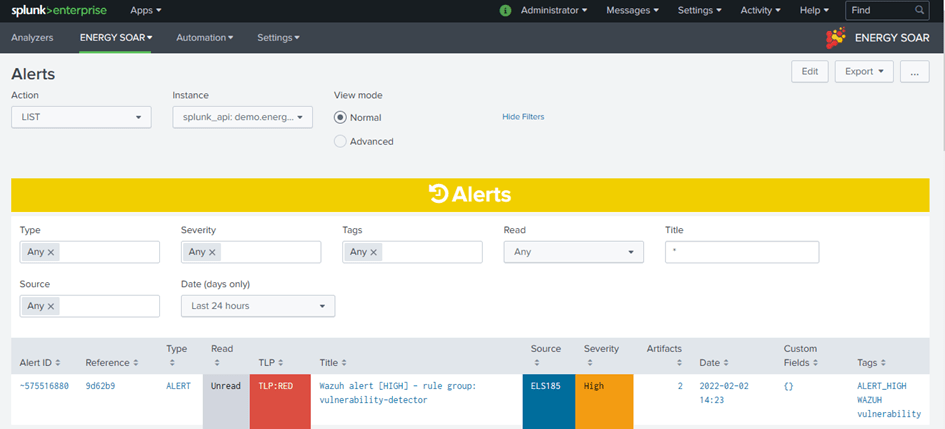
Alert ID: ID of the alert
Reference: the unique reference for this alert
Type: type of alert
Read: the status of the alert on Energy SOAR (unread, read, imported)
TLP: TLP of the alert
Title: Title of the alert
Source: the set source of the alert
Severity: Severity of the alert
Artifacts: number of observables in the alert
Date: date & time of the alert
Custom Fields: custom fields of the alert
Tags: Tags of the alert
You can set filters for the history:
Type: type of alerts
Severity: Severity of alerts
Tags: Tags of alerts
Read: read status of alerts
Title: Title of alerts
Source: source of alerts
Date: Creation date of alerts
Create a new alert
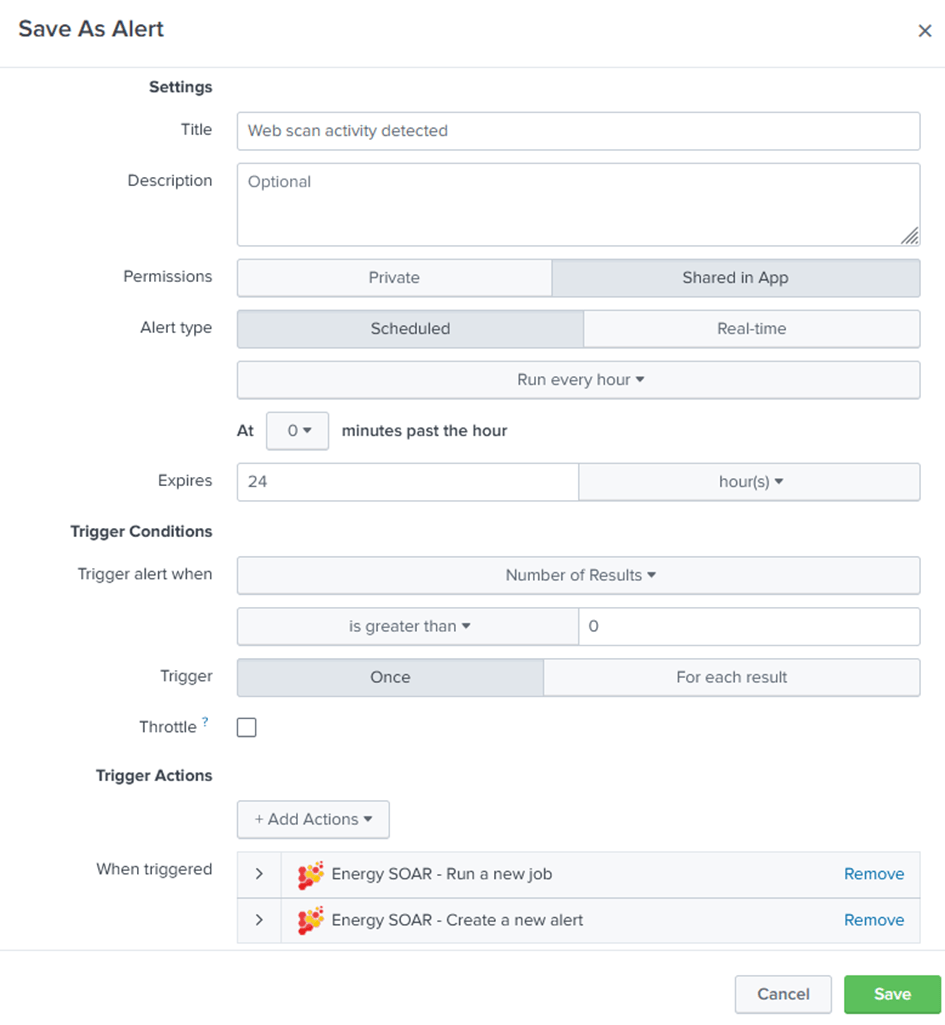
The standard way is to use the alert action “Energy SOAR – Create a new alert” in your saved Splunk alerts or correlation searches. You can manually create a new alert from Splunk using the “CREATE” action and a valid SID of a Splunk search.
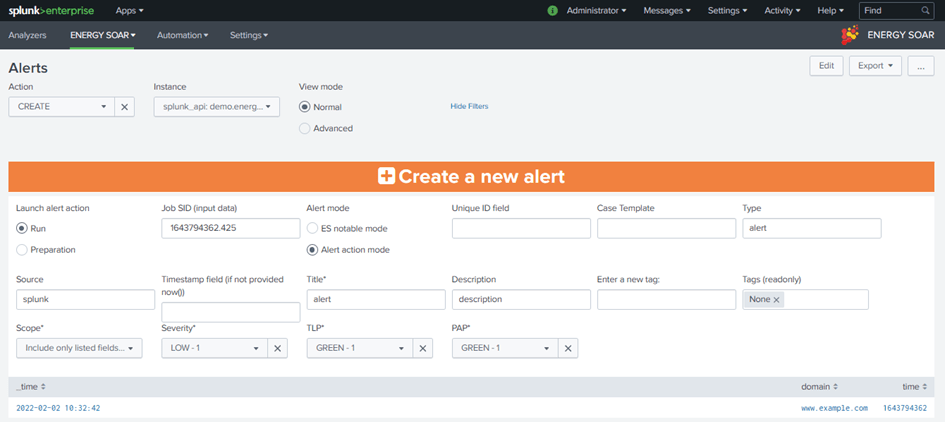
Job SID (input data): SID of a search (you can retrieve SIDs from Splunk > Activity > Jobs)
Title: Title for this new alert
Severity: Severity for this new alert
Tags: Tags for this new alert (they are added by specifying values in the “Enter a new tag” input)
TLP: TLP for this new alert
PAP: PAP for this new alert
Source: source of this alert (you can provide a field name to set this value from results)
Timestamp field: field containing a valid EPOCH timestamp (10-digit for s;13-digit for ms) – if not present, default to now()
Unique ID field: the unique reference for this alert. If a field name is provided, it is used to group results rows in several alerts – default is SPK+now()
Type: type of alert (default is “alert”)
Case Template: Case template to use by default when importing alert into a case
Description: Description for this new alert
The search will retrieve the results from SID and create the new alert. You can check the new alert in alerts list.
Automation Jobs dashboard
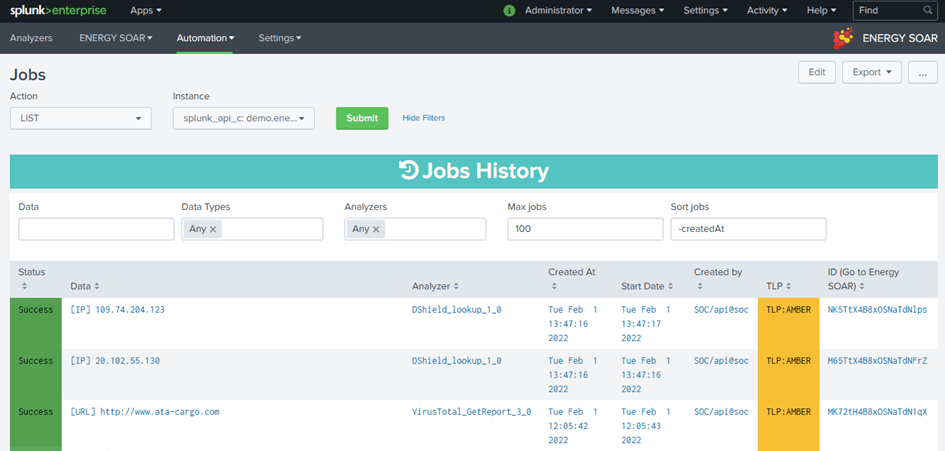
You can retrieve the history of jobs in Energy SOAR using the action “LIST”. For each job, you can see :
Status: Current status for the job
Data: Data and datatype for the job
Analyzer: Analyzer used for the job
Created At: Date and time for the creation of the job
Start Date: Date and time for the start of the job (a created job could not be executed immediately)
Created by: User/Organization used to created the job
TLP: TLP specified for the job
ID: ID of the job
You can click on the ID to view the result of the job directly on Energy SOAR
You can also set filters for the history.
Run new tasks
You can start new analysis from Splunk using the “RUN” action.
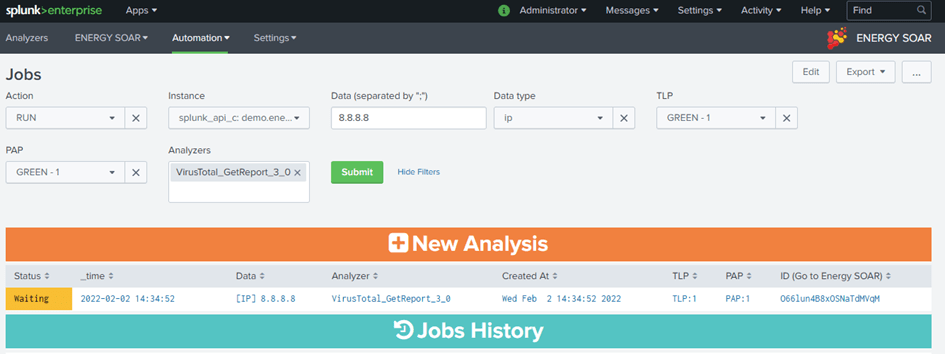
Data: data you want to analyze separated by a semicolon, they must be of the same data type
Data type: corresponding to the data type of data
TLP: TLP level to use for this analysis
PAP PAP level to use for this analysis
Analyzers: analyzers to use, if “any” is set, it will use any enabled analyzers for the given data type
The search will execute all jobs (one data with one analyzer) and return information such as the job ID.
Splunk alert actions
Alert actions help you respond to triggered alerts. You can enable the following actions:
· Energy SOAR – Create a new alert,
· Energy SOAR – Run a new job.