Can Energy SOAR query SIEM for additional information?
Sure! We can do it automatically using workflows.
SIEM alert enrichment
SIEM systems use correlation rules to monitor for specific events or set of events. Alerts trigger when search results meet particular conditions. You can also add actions to your alerts such as creating alert in SOAR when correlation rule triggers. Alert content can include observables such as IP, host or username.
Sometimes during alert investigation in SOAR you need to search logs in SIEM to get more information. You can switch to SIEM console, search data and continue investigation in SOAR.
If it is a repetitive action we can create a workflow to search the data automatically without the need for switching User Interfaces.
Domain-type observable
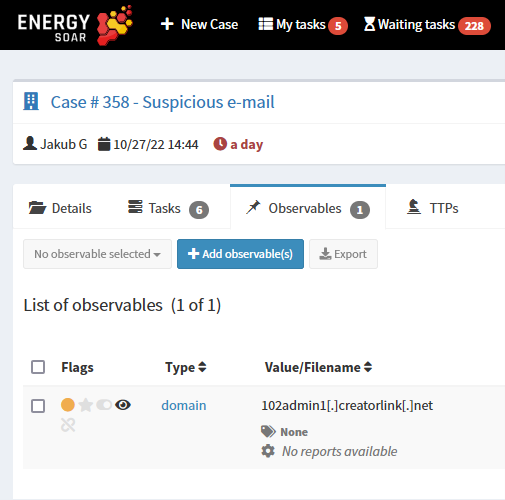
Let’s discuss the following example. We have Suspicious e-mail case. It Includes domain-type observable.
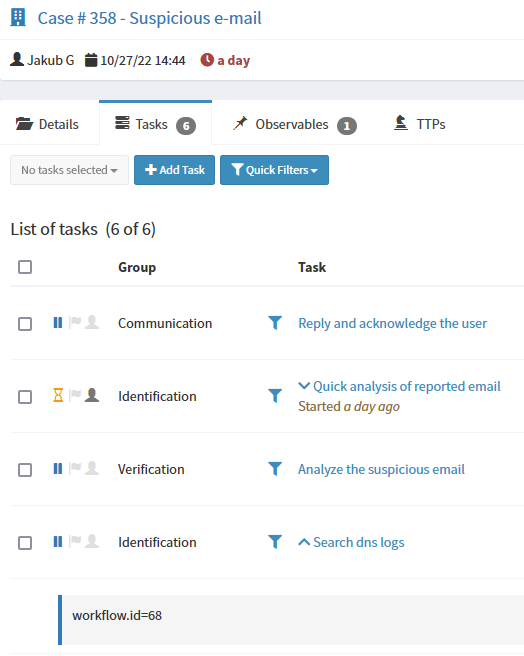
Search dns logs task
After checking domain’s reputation we want to find out if we can find it in our DNS server logs.
List of task contains Search dns logs task. It has workflow.id assigned.
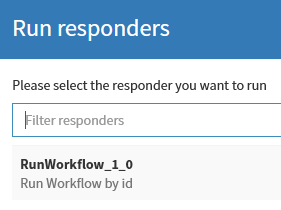
Run Workflow
In the task we can run responder RunWorkflow. It takes workflow.id from task’s description (synatax workflow.id=68 or workflow.id:68 is supported) and runs Search logs workflow.
Search dns logs workflow
Let’s discuss Search logs workflow. It get case details and extracts observables.
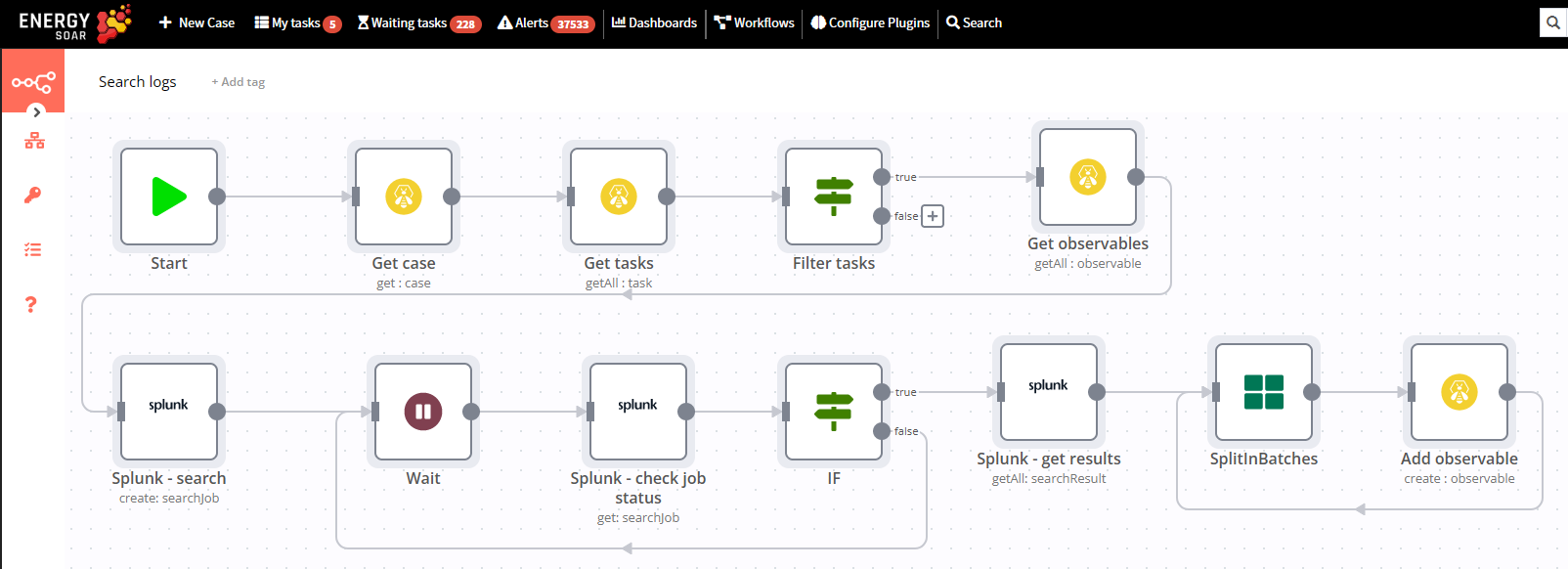
After that we execute search in SIEM – in this example Splunk.
In the node Splunk – search we create new search job, define query and time range e.g. a week ago.
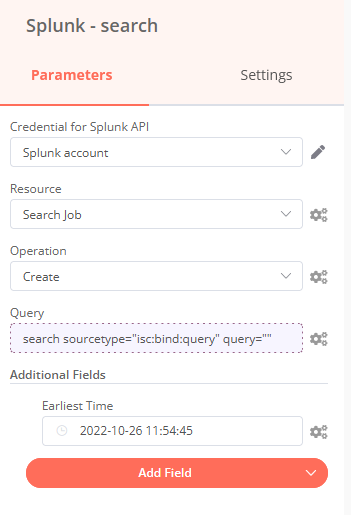
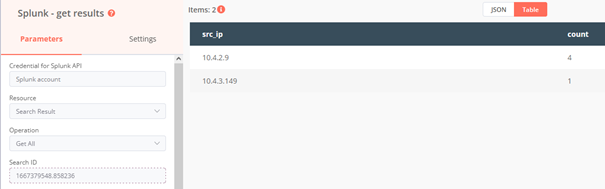
We want to search for the domain observable in ISC BIND logs to find out which DNS client send requests to ask for the IP address associated with the domain name:
search sourcetype=”isc:bind:query” query=”{{ $json[“data”] }}”
|stats count by src_ip
In the node Splunk – check job status we get search job details. If it’s undone we wait and check status in loop. When it’s completed we get job results in next node.
Final results
After that we want to add IPs as observables to the case. Each observable has dns_logs tag assigned.
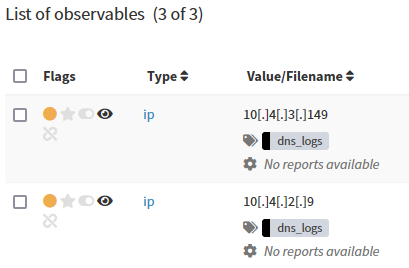
New observables are ready to take further investigation or running blocking actions.