According to ENISA Threat Landscape 2023 social engineering attacks grew significantly in 2023 but phishing remains the top attack vector. Phishing is once again the most common vector for initial access. Europol warned about the potential misuse of artificial intelligence-powered chatbot ChatGPT in phishing attempts. It helps in crafting more convincing emails and messages that closely mimic legitimate sources.
The attackers want to get valuable information such as credit card numbers and credentials. Most credentials attackers obtain using stealer malware. The stealers commonly find their way to victims’ machines via phishing. In the past phishing campaigns relied on document macros to get malware executed. Blocking macros coming from the Internet made this technique obsolete. Threat actors switched to compressed files, containers and LNK shortcuts.
Phishing-as-a-Service has further amplified the reach of social engineering attacks. It provides individuals with even minimal knowledge of cybersecurity the means to execute a complex phishing attack.
You can use Energy SOAR to mitigate phishing attempts. Users can be trained to identify social engineering techniques and phishing emails. If they are not sure they forward suspicious messages to dedicated mailbox, which is monitored by SOAR.
The case
When a new message arrives, SOAR creates a case and original message is saved as file-type observable.
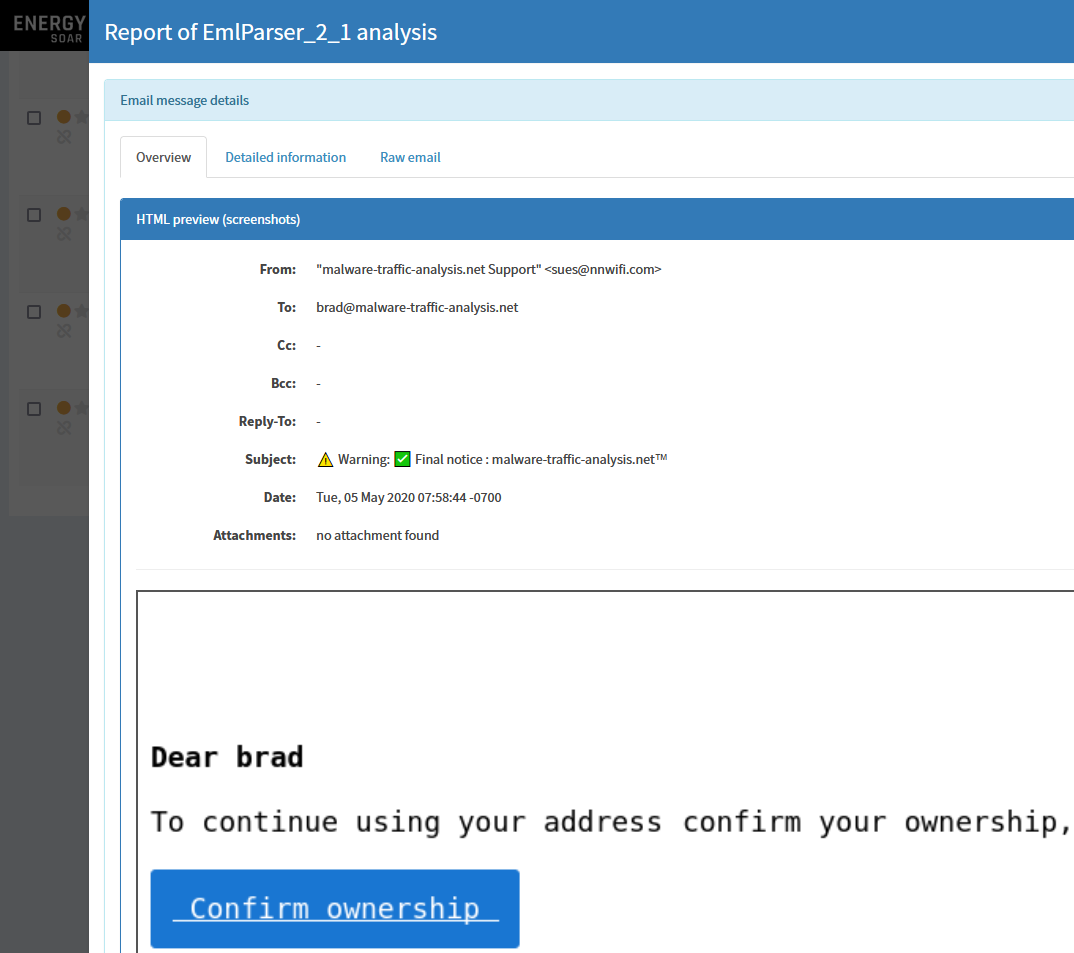
Directly in Energy SOAR console you can see all details including raw email and HTML preview:
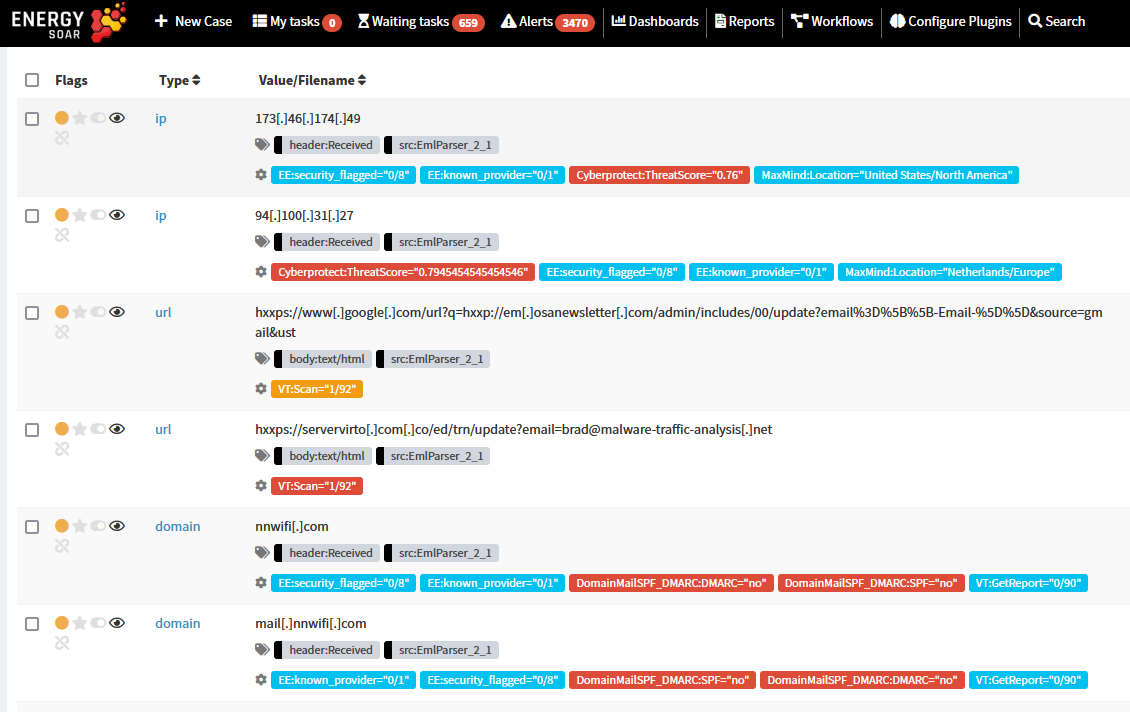
EML parser also extracts all relevant information such as IPs, URLs, domains, email addresses, attached files hashes.
Orchestration
Using analyzers you can quickly check these objects to know their reputation.
Automation
Ready to use workflows lets you automatically analyze objects and calculate risk for entire message.
The workflow has the following risk thresholds set:
- 0% – notify employee “Message safe”,
- 0-10% – notify SOC: Message requires further validation,
- > 10% – notify employee “Message malicious” and block sender or links.
If the risk is between 0-10% system, before notifying SOC, will automatically search for similar cases that have been analyzed recently. If there is a match then SOAR will get the verdict.
If the company conducts phishing simulations, you can easily exclude those messages from processing. You can also exclude other types of messages relevant to your organization which are sent periodically.
Suspicious email cases contain the following tasks:
- Communication – contents of external message, which includes EML file for analysis.
- Reply and acknowledge the user.
- Quick analysis of reported email.
- Analyze the suspicious email.
- Search proxy logs.
- Block e-mail.
- Before closing the case.
- Request eml.
- Notify user – email message ok.
- Notify user – email message SPAM.
Some of the tasks lets you run RunWorkflow responder to take relevant actions:
- Request eml – an analyst can send request to employee for EML file attachment.
- Block e-mail – block sender on the gateway.
- Notify user – email message ok – Notify user that message is safe if positively assessed by the analyst.
- Notify user – email message SPAM – block sender on the gateway and notify user that message is SPAM.
Analysts can run manually above actions if needed.
Scanning email attachments or links can be used to block malicious objects and protect users.
SOAR plays a crucial role in improving an organization’s ability to detect, respond to, and mitigate attacks through automation, orchestration, and integration with other security tools and processes.