SIEM systems are crucial tools in cybersecurity for monitoring and detecting security threats. They collect and analyse data from various sources within an IT environment, such as network devices, servers and security devices.
Correlation rules are predefined logical statements used by SIEM systems to identify patterns that may indicate security threats or malicious activity. These rules combine different types of data from various sources to detect complex attack patterns that may not be obvious when looking at individual events. When a correlation search matches the conditions specified in the rules, the SIEM system triggers an alert.
Empowered AI: AI in the forecasting & anomaly detection service
Empowered AI from Energy Logserver is innovative solution based on machine learning. It provides comprehensive protection against advanced and dynamically changing cyber threats.
Use of machine learning algorithms for threat analysis and prediction, affects early detection of potential attacks based on numerical and textual analysis. Identification of anomalies in data sets, helps in rapid detection of threats and optimizing response.
AI alert rules can help to detect various events such as:
- Long-term connections with bad IPs,
- Network baseline anomalies,
- Increase in the number of packets that were sent by the device,
- Increase in the amount of data that was transferred by the device,
- Excessive increase in the number of connections,
- Network communication with unusual countries.
Alert
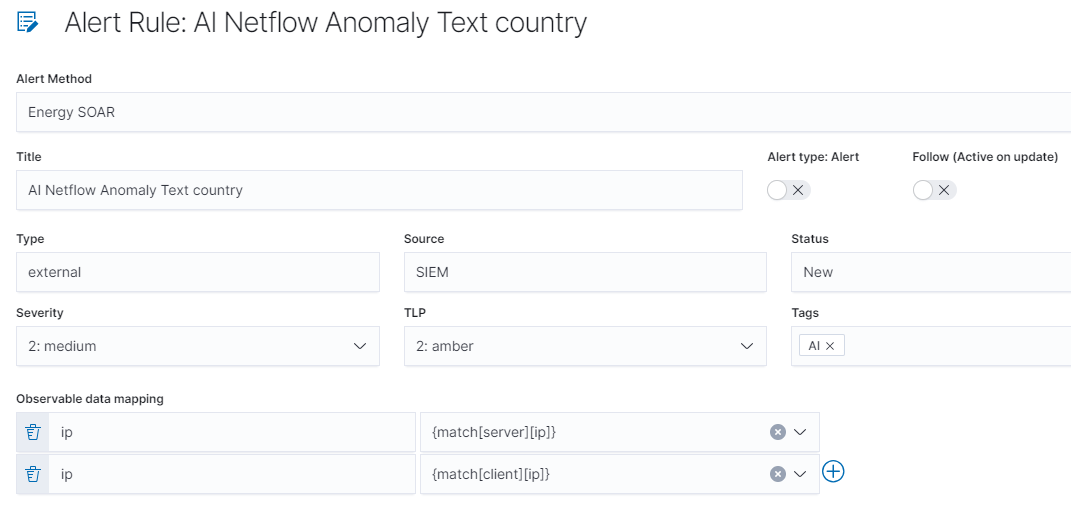
Let’s discuss handling Netflow Anomaly Country alert. During alert configuration in Energy Logserver we choose Energy SOAR alert method to pass alerts to SOAR for further investigation.
In observable data mapping section we select both client and server IP.
Analysis
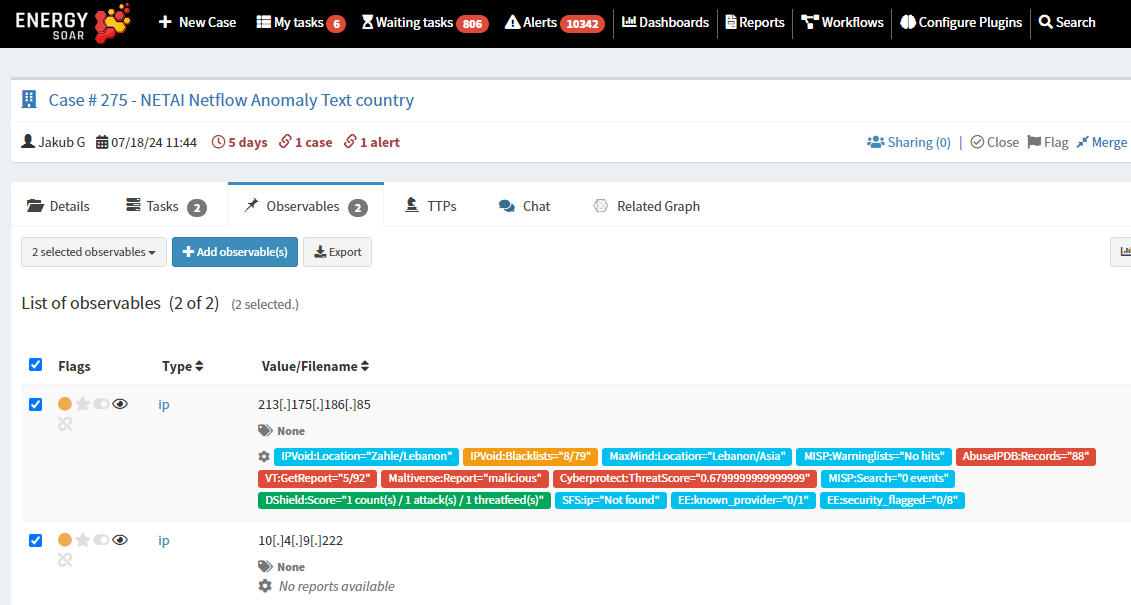
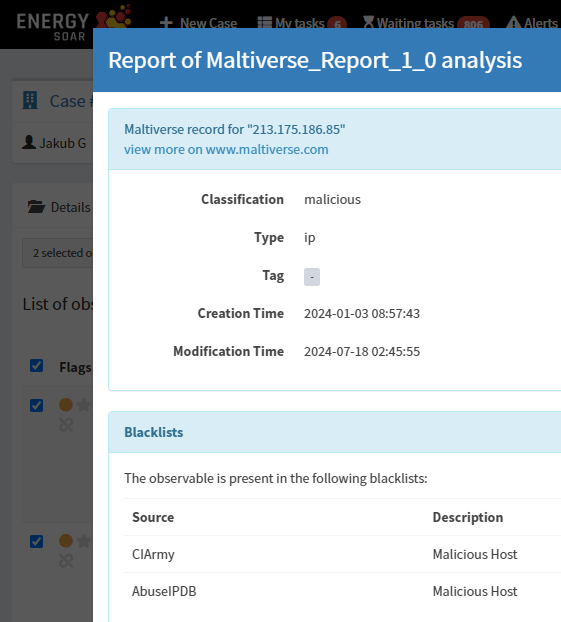
Energy SOAR orchestration capability lets us gather additional context about the public IP observed in the alert. This can include:
- Threat Intelligence Feeds: Querying threat intelligence sources to check if the IP address is known for malicious activity.
- Reputation Services: Checking IP reputation databases to assess the threat level of the IP.
- Geolocation Services: Determining the geographic location of the IP address to see if it matches expected patterns or regions.
The drill-down allows an analyst to display additional details if needed.
Response
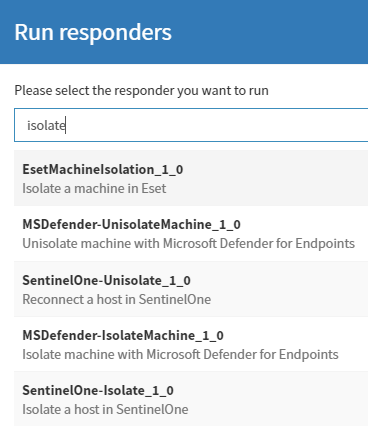
We can use responders to mitigate the detected threat:
- Firewall Block IP: To prevent further malicious activity from a specific IP address by blocking it at the network perimeter.
- Workstation Isolation: To contain the threat within a compromised workstation, preventing lateral movement and further infection across the network.
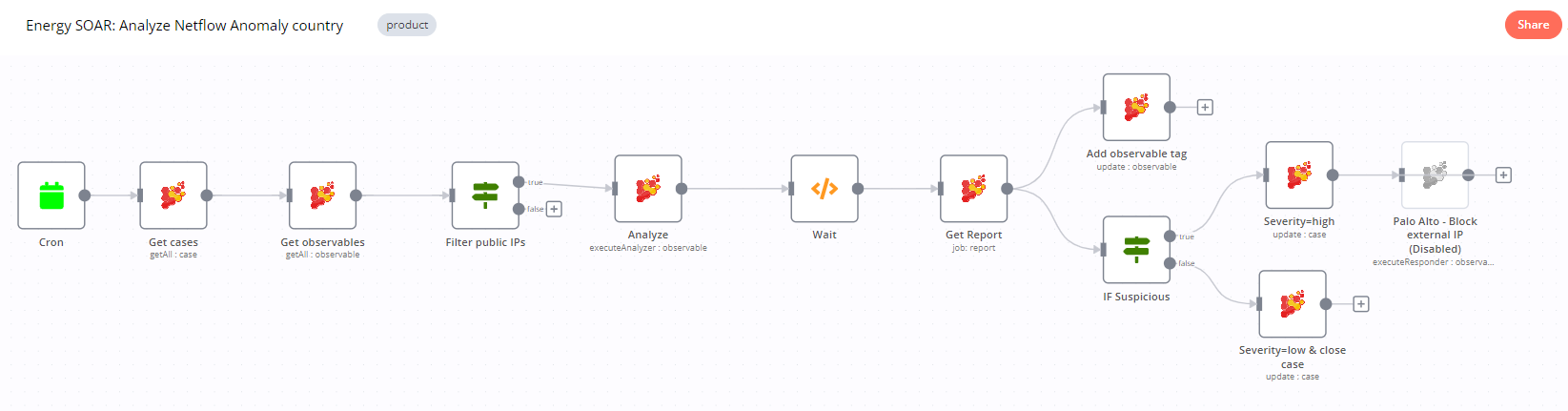
Automation
Energy SOAR workflow is a sequence of automated steps designed to handle security incidents efficiently. These workflows can be customized to suit the specific needs and processes of an organization. They integrate various security tools and data sources to streamline and automate the tasks involved in threat qualification, investigation, and response.
So Energy SOAR can analyse alert objects and based on the gathered data take appropriate actions such as blocking IP.
Automated alert assignment
Automated alert assignment is a key feature in SOAR systems designed to optimize the distribution of alerts and incidents among security analysts. This ensures a balanced workload and improves the efficiency and effectiveness of incident response. Build-in automation rules can assign new alerts to specific analysts based on their expertise, current workload (number of open cases) and historical performance metrics.
Benefits of AI in SIEM and SOAR
To summarize let’s point out key benefits of AI in SIEM and SOAR:
- Enhanced threat detection: AI can analyse vast amounts of data to identify deviations from normal behaviour, spotting potential threats that traditional rule-based systems might miss.
- Workflow automation: AI can execute predefined playbooks for incident response, automating routine tasks and reducing the response time.
- Workload management: AI can balance workloads by assigning incidents to analysts based on their current load and expertise, ensuring efficient resource utilization.
- Improved accuracy and efficiency: AI reduces the manual effort required for threat detection and response, allowing analysts to focus on more complex tasks.