Technical accounts are quite often used for API access. You can create a correlation rule in your SIEM to detect a login attempt from different than usual client IP which could mean a breach or a misuse.
Let’s create a SOAR workflow to handle these alerts. In this scenario we want to automatically ask technical account owner to confirm the account usage.
It starts with case created by SIEM. It contains username, hostname and client IP.
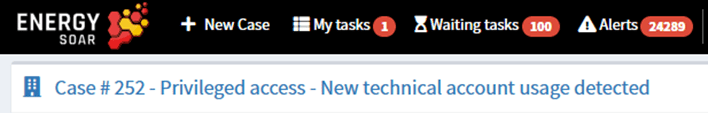
It’s our new workflow.
Let’s go through nodes used by the workflow.
Get observables / Pass username
Take observables from the case and select username.
Read binary file / Spreadsheet file
Read list of tech accounts and their owners. Can be replaced by database query.
Select username
Match username from the case and the file.
Get tasks and Update task
Get tasks from the case and change status of the task „Verify activity with relevant system administrators”.
Send email
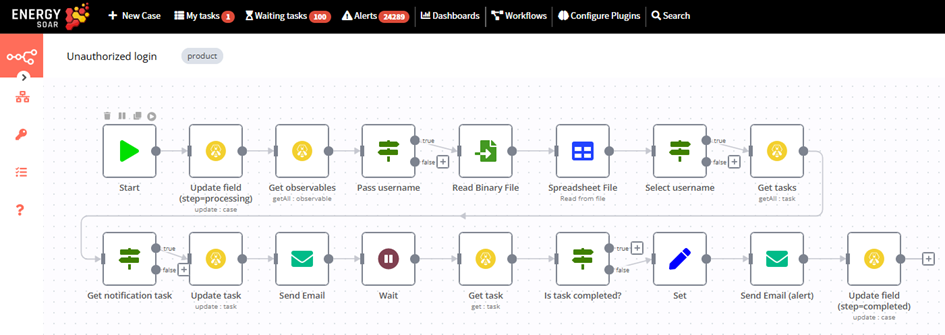
Send email to account owner with confirmation link.
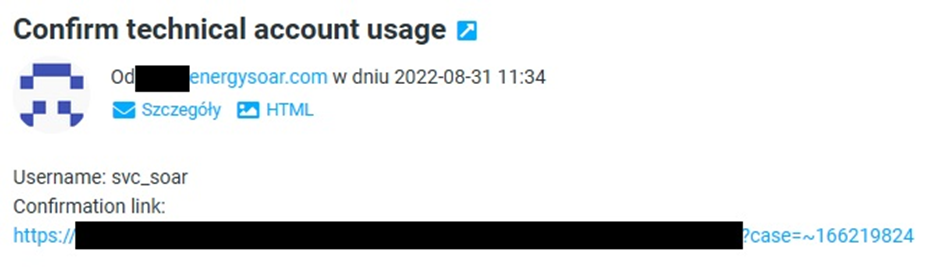
If administrator confirms technical account usage then SOAR runs supporting workflow „Trigger – Unauthorized login”. The first node starts the workflow when a webhook is called. Then status of the task becomes completed.
If administrator doesn’t confirm technical account usage within wait time period then the task „Verify activity with relevant system administrators” isn’t completed.
After that SOAR sends email notification „Unauthorized login not confirmed”. Some may say „Unauthorized login” isn’t automatic workflow because it begins with Start node. Best practice is to build small and modular playbooks which are easier to maintain. Energy SOAR executes workflows using global trigger. It starts appropriate workflows when case created events