Another day in the SOC office. IT Security that was supposed to be challenging and interesting become repetitive and … boring. Same Alerts every day to analyse. Analyze the attachement, check IP reputation, check file hash, has anyone seen it? You know what I mean? Hope NO, because if YES, than we have little time before complete frustration.
Let play and automate our security analytics !
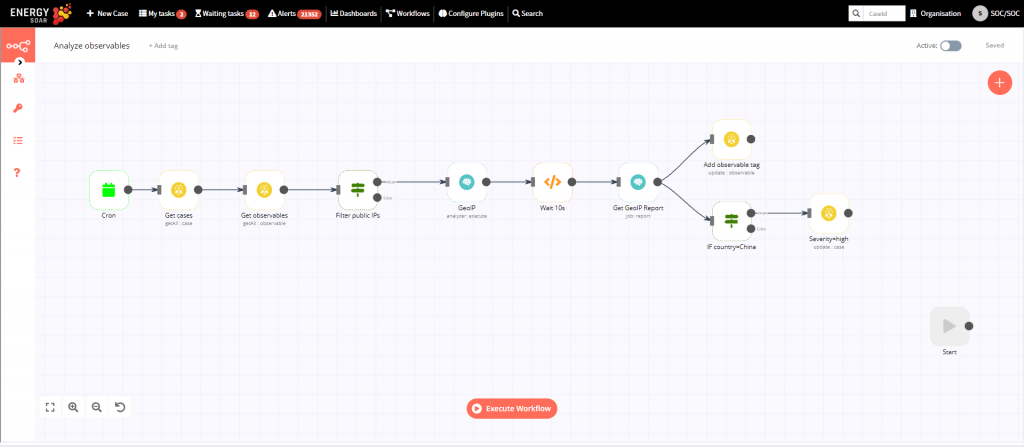
SOC analysts have to handle many repetitive tasks. With Energy SOAR you can build workflows to automatically execute all relevant actions. In this example we analyse IP addresses and update cases.
Let’s go through all the nodes You see on automated workflow.
Cron
This is the starting point. Beloved crontab. This node is useful to schedule the workflow to run periodically at fixed dates, times or intervals.
Get cases
Next we search open cases which have automation tag.
Get observables
Take observables from cases for automation.
Filter public IPs
In next step we choose observables which are only public IP addresses because we don’t want to analyze our local network information.
GeoIP
In this step we run MaxMind GeoIP analyzer to get IP geolocation data.
Wait 10s
Before further proceeding we have to wait a while for GeoIP report to become available.
Get GeoIP Report
Next we get GeoIP report which provides country and city of analyzed IP addresses.
Add observable tag
We put country information into observables tag field.
IF country=China / Severity=high
If country is China then change severity of the case to level high.
Orchestration & automation from Energy SOAR reduce time required for handling incidents. Automating repetitive tasks lets you focus on deeper analysis and threat hunting.