
Security Operations Center (SOC) staff face a daunting challenge – managing thousands of alarms generated by SIEM (Security Information and Event Management) systems. This overwhelming volume often leads to ignored alarms, which can be dangerous. Hence, focusing on the quality rather than the quantity of alerts becomes crucial.
A prime example of effective SIEM alarm optimization is the use of SOAR technology for enhancing these alarms.
For instance, XDR provided by Energy Logserver SIEM alerts about changes in port listening activities. In most cases, these alerts result from normal operations of services on a device. To address this issue, we conducted a thorough analysis and created a whitelist of services that typically operate on specified hosts.
This process of analysis and creating exclusion lists significantly reduced the number of irrelevant alerts. In just three days, we reduced the number of alarms from 1253 to just four, which indeed indicated potential threats.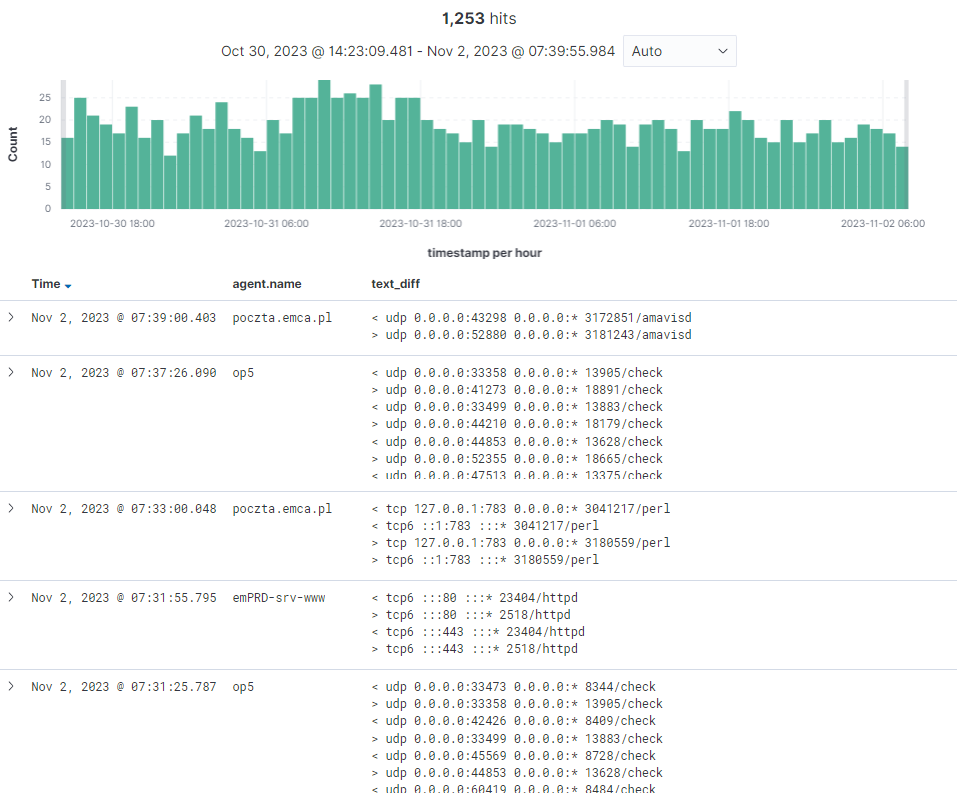
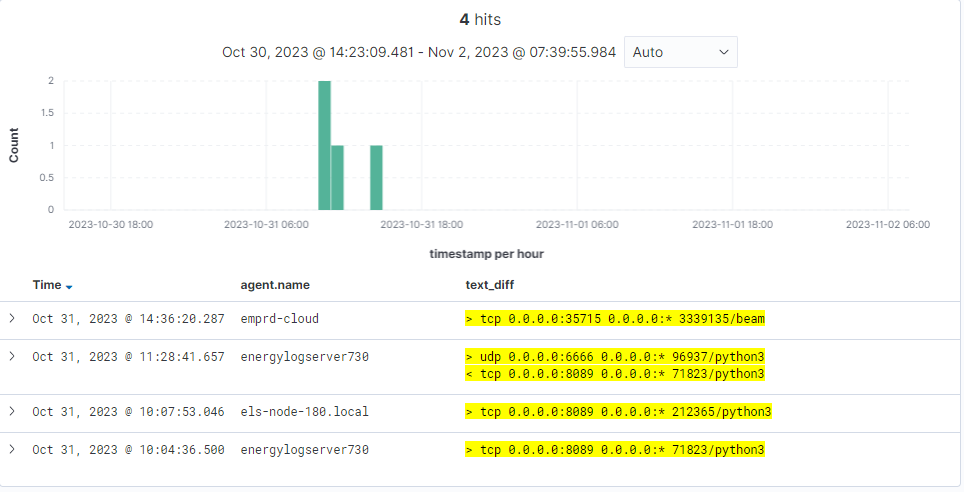
But how exactly does the improvement process work? Here, SOAR (Security Orchestration, Automation, and Response) technology plays a crucial role, allowing control over the alert optimization process in Energy Logserver SIEM. Take, for example, an alert about a newly opened port – a key element of network security.
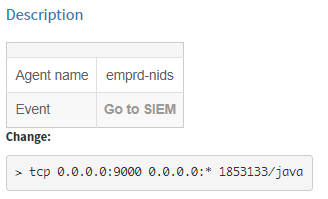
After thorough verification, such an alert may turn out to be a false alarm, as the service in question is acceptable on the server. In this case, we appropriately modify the alert rule, record the action in the incident management system, and close the alert as a false positive.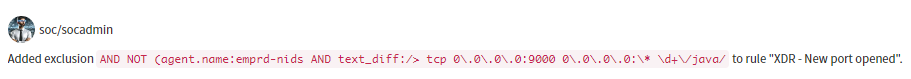
Going from 1253 alarms to just 4 in three days is a significant difference. Imagine the need to manually verify each of these thousand open ports. SOAR offers not only automation but also the enhancement of existing alarm rules, enabling security analysts to focus on detecting and responding to real threats.
In an era of increasing cyber threats, efficient security alert management is key. Optimizing SIEM alarms using Energy SOAR technology is an excellent example of how modern tools can revolutionize SOC work, increasing efficiency and effectiveness in detecting and responding to digital threats.