It’s important to track suspicious administration activities such as newly created accounts that have been elevated to local administrators. Many organizations keep a small number of local admin accounts used for particular applications or for access in the case of domain controller connectivity issues. However malware, malicious intruders and even insiders create local admin accounts.
You can easily build a corelation rule in your SIEM to detect these actions but how to respond? Contact the owner of the system to confirm if a new user was added to security enabled group. Let’s do it automatically in Energy SOAR.
It starts with case created by SIEM. It contains new admin username and the user account that created it.
It’s our new workflow.
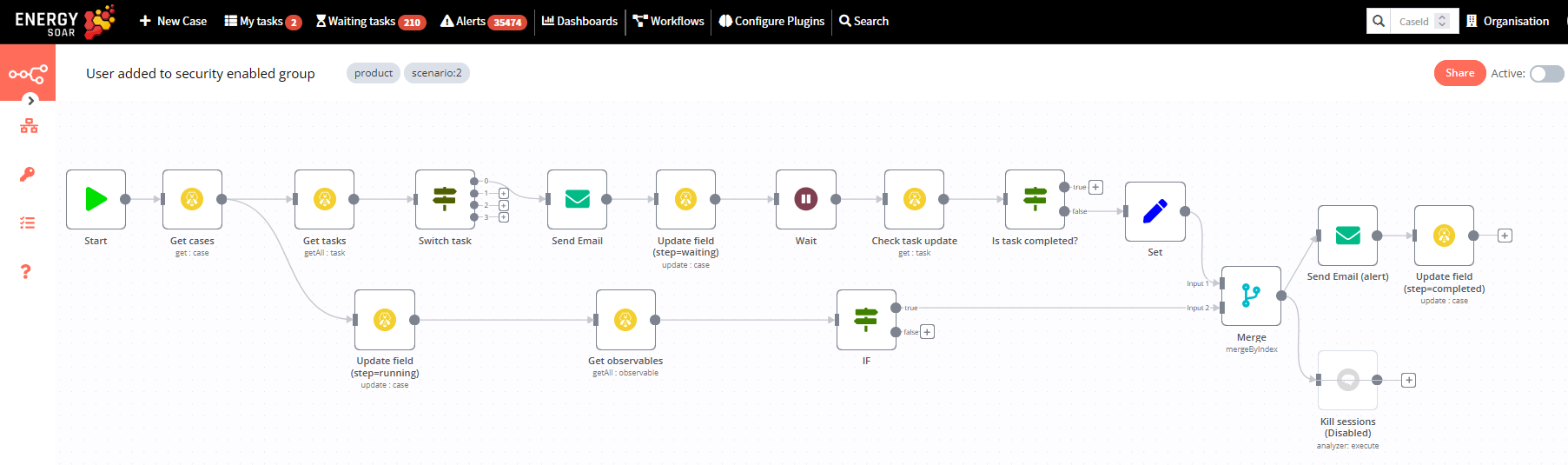
Let’s go through nodes used by the workflow.
Get cases / Get tasks / Switch task
Read case, take tasks list and select task „Confirm creation”.
Send email
Send email to administrator with confirmation link.
Wait
Wait for the confirmation.
If administrator confirms new account creation than SOAR runs supporting workflow „Webhook – confirm user creation”. The first node starts the workflow when the webhook is called. Then status of the task becomes completed.
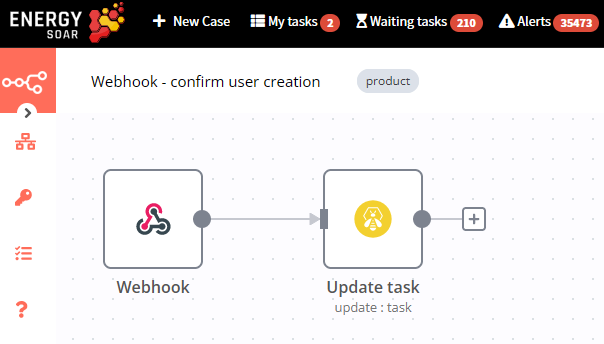
If administrator doesn’t confirm the activity within wait time period then the task „Confirm creation” isn’t completed.
After that SOAR sends email notification „User creation was not accepted” for additional investigation. We can also enable kill session response.
Using the automatic workflow you can clear most of “User added to security enabled group” alerts and focus on deeper analysis.