Every time Soar travels through the data it collects crucial keys needed in orchestration and automation process. Integrated SIEM is a source of alerts from which SOAR generate its knowledge. EnergySoar is no different. From ingested alerts we collect our Observables. What are they ?
Very simple, Observables are pieces of information added to a case.
Anything important, extracted from Alert like:
| autonomous-system | fqdn | registry | |
| domain | hash | mail-subject | uri_path |
| file | hostname | other | url |
| filename | ip | regexp | user-agent |
Types of observables
EnergySoar user can create observables automaticly and manually. Lets perform the following steps to add an observable:
1. Click Add observable(s) button:
![]()
2. Create new observables(s) window appears:
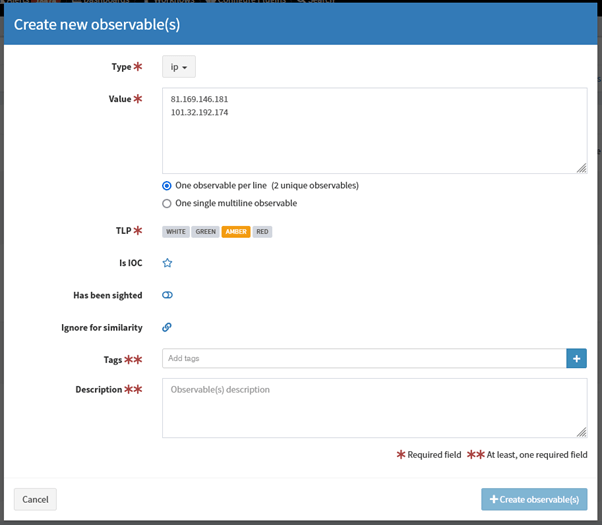
Creating new observables
3. Select type e.g. ip, domain, url, mail.
If you choose file type, you can upload a file. Zipped archives are supported.
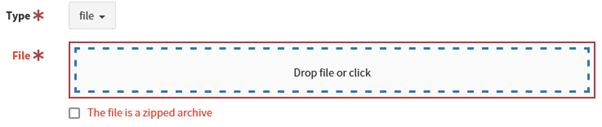
4. You can add one single observables or many observables at once – one observable per line.
5. Select appropriate TLP
6. (Optional) IOC flag indicates observables classified as True Positive. Only IOC-flagged observables are exported to MISP instances.
7. (Optional) You can also set “Has been sighted” toggle to mark observables which have been seen.
8. (Optional) If you click “Ignore for similarity”, you will disable “Observable seen in other cases” list.
9. Add tags and/or description.
10. Click Create observable(s).
On Observable List you can check if observables have been seen in other cases:
- Black eye: Observable seen in other cases,
- Red eye: Observable seen in other cases and flagged as IOC there.
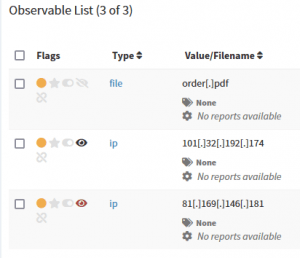
You can display details and check cases where the observable has been seen:
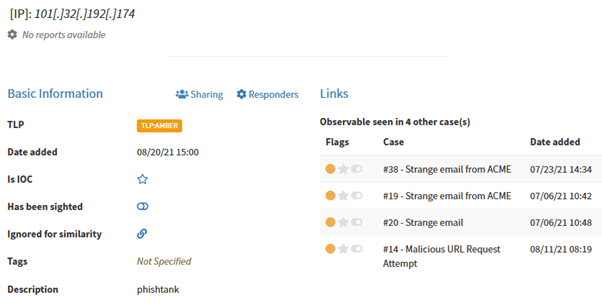
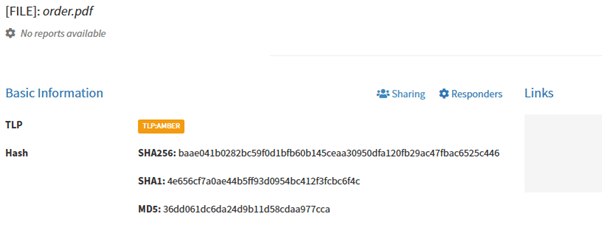
After uploading file-type observables hashes are automatically calculated:
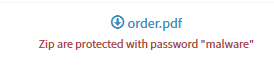
If you want to download file observable, it will be zipped and password protected:
Now You can run various analyzers (e.g. VirusTotal, MaxMind_GeoIP) and responders (e.g. block IP, domain, e-mail) against Your observables.